Sysdig
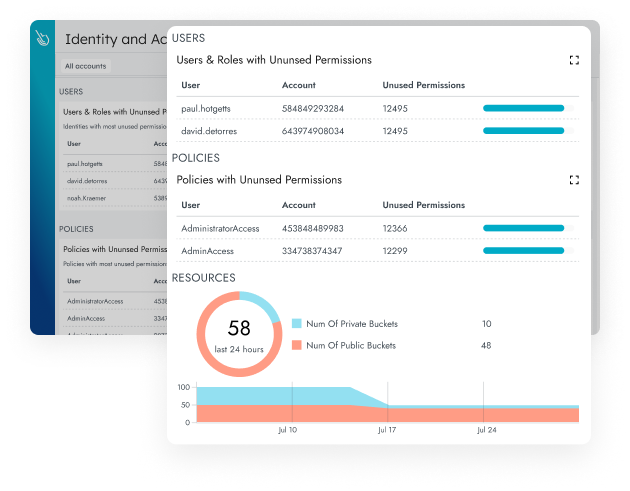
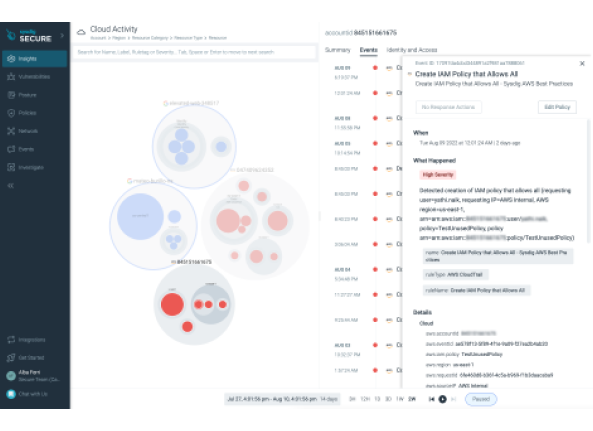
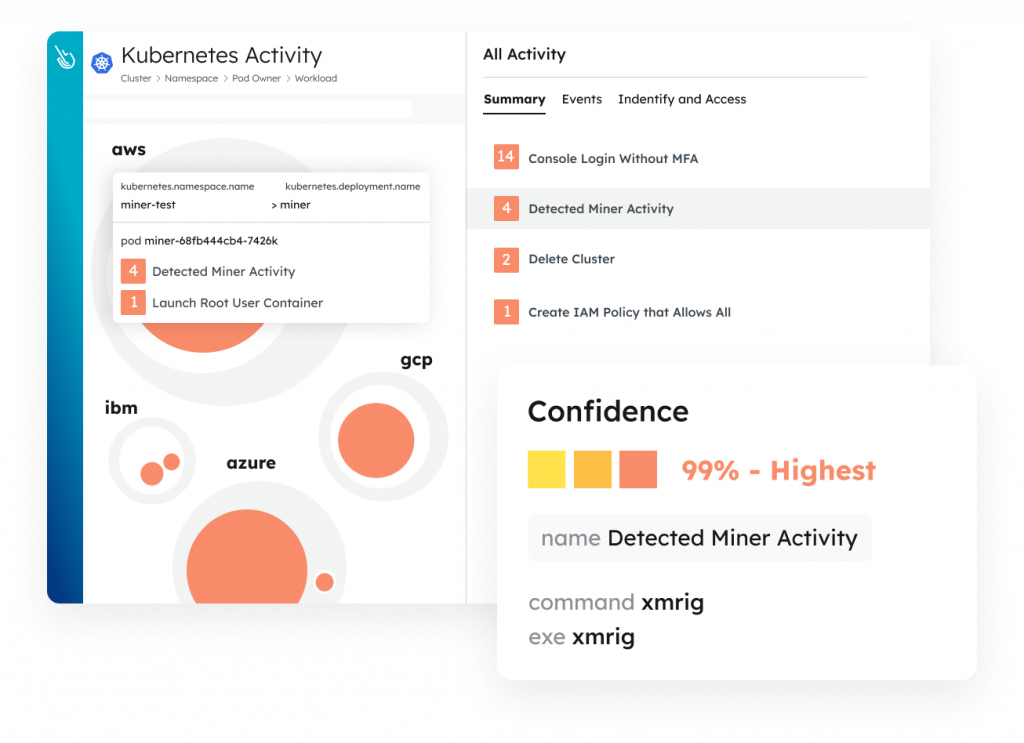
Sysdig is a cloud security and monitoring platform used in Kubernetes, Docker, and other container platforms. Sysdig offers a range of features to ensure the security, monitor the performance, and diagnose issues of applications running in the cloud environment. Some key features provided by Sysdig include Cloud Detection and Response (Workload Security), Permissions & Entitlement Management, Vulnerability Management for Containers and Hosts, Posture Management, and End-to-End (From Source to Run) Cloud Security